Vulnerability management is a continuous and proactive process that identifies, assesses, prioritizes, and mitigates vulnerabilities to keep your computer systems, networks, and applications safe from cyberattacks and data breaches.
When vulnerabilities go unresolved, cybercriminals can exploit them to breach critical systems, steal sensitive data, and disrupt business operations. These situations highlight the importance of robust vulnerability management practices.
The main goal is to lower risk exposure by fixing as many vulnerabilities as possible.
This article dives deep into vulnerability management, explaining:
- What it is and how it works
- Why it’s crucial for your business security
- Step-by-step process of vulnerability management
Vulnerability Management: Your Shield Against a Growing Threat Landscape
Let’s face it, headlines about cyberattacks are all too common these days. But the statistics paint an even more alarming picture. According to Hiscox, 41% of small businesses were hit by cyberattacks in 2023, up from 38% in 2022 and almost double the 2021 figure.
The financial impact is just as concerning. US small businesses paid over $16,000 on average in cyber ransoms last year alone. This doesn’t include the cost of downtime, data recovery, or legal consequences post-breach.
The rise in cyberattacks targeting small businesses isn’t a coincidence. Attackers see them as easier targets than larger companies with strong security. Unfortunately, many lack the resources and expertise needed to fight back.
The good news? Vulnerability management is a powerful defense by regularly scanning your systems for weaknesses. You then address these vulnerabilities, staying ahead of potential threats.
Before anything else, let’s first discuss some cybersecurity basics.
Differentiating Vulnerability, Threat, and Risk
These cybersecurity terms are often confused to mean the same. To understand the differences, let’s define vulnerability, threat, and risk.
- Vulnerability: A weakness in your system’s defenses, e.g. outdated software or weak passwords. These are exploitable gaps in your security.
- Threat: A potential danger that could exploit vulnerabilities, such as malware attacks or phishing attempts. These are malicious actors looking to cause harm.
- Risk: Measures the possibility of a threat exploiting a vulnerability and the damage it could cause. Risk is the potential harm that arises from the combination of vulnerability and threat.
Think of vulnerabilities as weaknesses, threats as potential attackers, and risk as the combined danger they pose.
Causes of Vulnerabilities
Vulnerabilities can stem from various sources, including:
- Hardware vulnerabilities stem from outdated components, firmware neglect, or misconfigurations.
- Software vulnerabilities arise from unpatched software, outdated applications, and insecure coding practices.
- Network issues include insecure configurations, weak passwords, open ports, and a lack of network segmentation.
- Organizational factors could be poor cybersecurity policies, inadequate training, low-security awareness, and insufficient access controls
Knowing how your systems can be attacked helps you take proactive measures to fix and strengthen your defenses.
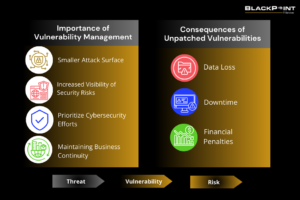
Why is Vulnerability Management Important for Your Business
Unpatched vulnerabilities = security gaps. Vulnerability management helps you close these gaps, directly benefiting your business by:
- Smaller Attack Surface: Regular checkups (vulnerability assessments) and simulated attacks (penetration testing) uncover weaknesses early. By fixing vulnerabilities, you minimize the entry points attackers can use to infiltrate your systems.
- Increased Visibility into Security Risks: Vulnerability management keeps you informed with accurate, real-time reports on your security status. Regular vulnerability scans give you greater visibility into your overall security posture. They not only spot current vulnerabilities but also help predict future risks.
- Prioritize Cybersecurity Efforts: Ranking vulnerabilities by severity lets you focus on mitigating the most critical issues. It allows for efficient resource allocation and systematic defense strengthening, creating a more secure environment.
- Maintaining Business Continuity: Addressing vulnerabilities promptly prevents disruptions to your operations. It ensures critical systems remain available and minimizes potential impacts from cyber incidents, such as financial losses and reputational damage.
Consequences of Unpatched Vulnerabilities
Failing to address vulnerabilities in your computer systems can have severe consequences for your business, such as:
- Data Loss: Cybercriminals exploit vulnerabilities to access sensitive information like customer data and financial details.
- Downtime: System failures caused by cyberattacks can cause downtime in critical operations. This can slow down your employees, hurt customer service, and cost you money in lost productivity.
- Financial Penalties: Failing to address vulnerabilities can lead to non-compliance with data protection regulations, incurring hefty fines from regulators.
Vulnerability Management Process
Having established the critical role of vulnerability management, let’s explore the process itself.
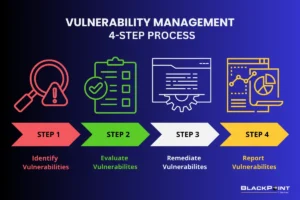
1. Identify Vulnerabilities
Identifying vulnerabilities is like giving your systems a thorough security checkup. Automated vulnerability scanning tools find potential weaknesses across systems, networks, and applications. They check hardware, software, and network configurations for gaps attackers could exploit. When a vulnerability is detected, the scanner flags it for remediation. The goal is to provide detailed reports that pinpoint vulnerabilities.
2. Evaluate Vulnerabilities
Once potential vulnerabilities and misconfigurations are identified, they undergo validation to confirm them as true vulnerabilities. They are then rated according to risk and prioritized based on these risk ratings. This process ensures a focused approach to addressing the most critical security risks.
Vulnerabilities are prioritized based on severity, exploitability, and potential impact:
- Severity: How easily can attackers exploit this vulnerability?
- Exploitability: Are there readily available tools or techniques to exploit it?
- Impact: What damage could occur if attackers exploit this vulnerability, such as data loss or system downtime?
3. Remediate Vulnerabilities
This means taking corrective actions to address vulnerabilities found in your system. Common techniques include patching software, configuration changes, upgrading hardware, and implementing security controls.
You can choose between full remediation, mitigation, or acceptance of vulnerabilities based on their risk assessment.
- Full remediation is the ideal solution—patching or completely fixing the vulnerability to eliminate the risk. After remediation, conducting a vulnerability scan ensures that all vulnerabilities are effectively eliminated.
- Mitigation aims to decrease the possibility of exploitation or minimize potential damage temporarily until a permanent fix is available.
- Acceptance can be an option when leaving a vulnerability unaddressed for the time being is acceptable. This could be because the vulnerability is not a significant threat to your systems or because the cost of resolving it is too high. In such cases, it may be better to acknowledge the vulnerability and continue searching for a more cost-effective solution in the future.
4. Report Vulnerabilities
Regular vulnerability scans and reports act as ongoing security briefings. They provide valuable insights into your overall security health, emerging threats, and trends in vulnerabilities. This allows your organization to stay proactive in managing cybersecurity risks, track progress, and allocate resources effectively.
It also fosters transparency and accountability by documenting details, remediation progress, and recommendations for IT managers and security officers.
You can establish an effective vulnerability management program by following these four steps—identify, evaluate, remediate, and report. This proactive approach will significantly reduce the risk of cyberattacks and keep your organization safe and secure.
What Can BlackPoint IT Do to Help
BlackPoint IT offers comprehensive cybersecurity solutions to protect your digital assets and take the security burden off your shoulders.
Here’s what you get with BlackPoint IT:
- Expert Cybersecurity Team: Our cybersecurity experts will take care of the overall vulnerability management process.
- Custom-tailored Tech Solutions: We don’t offer a one-size-fits-all approach. Our cybersecurity experts will customize a plan to address your specific business needs.
- Ongoing Support: We’ll be there every step of the way, offering guidance and expertise to keep your defenses strong and your vulnerability management program effective.
Ready to be proactive about cybersecurity? Schedule an initial free consultation today and find out how you can ensure protection of your critical business data and assets.




