
We identify and assess potential threats and vulnerabilities to your systems, networks, and data. Our team prioritizes resources and implements appropriate security controls to mitigate risks and protect your IT environment.

Compliance with regulatory standards is an essential component of a cybersecurity strategy. BlackPoint’s experts implement the necessary controls to ensure compliance with HIPAA, CMMC, NIST standards, and other security frameworks.
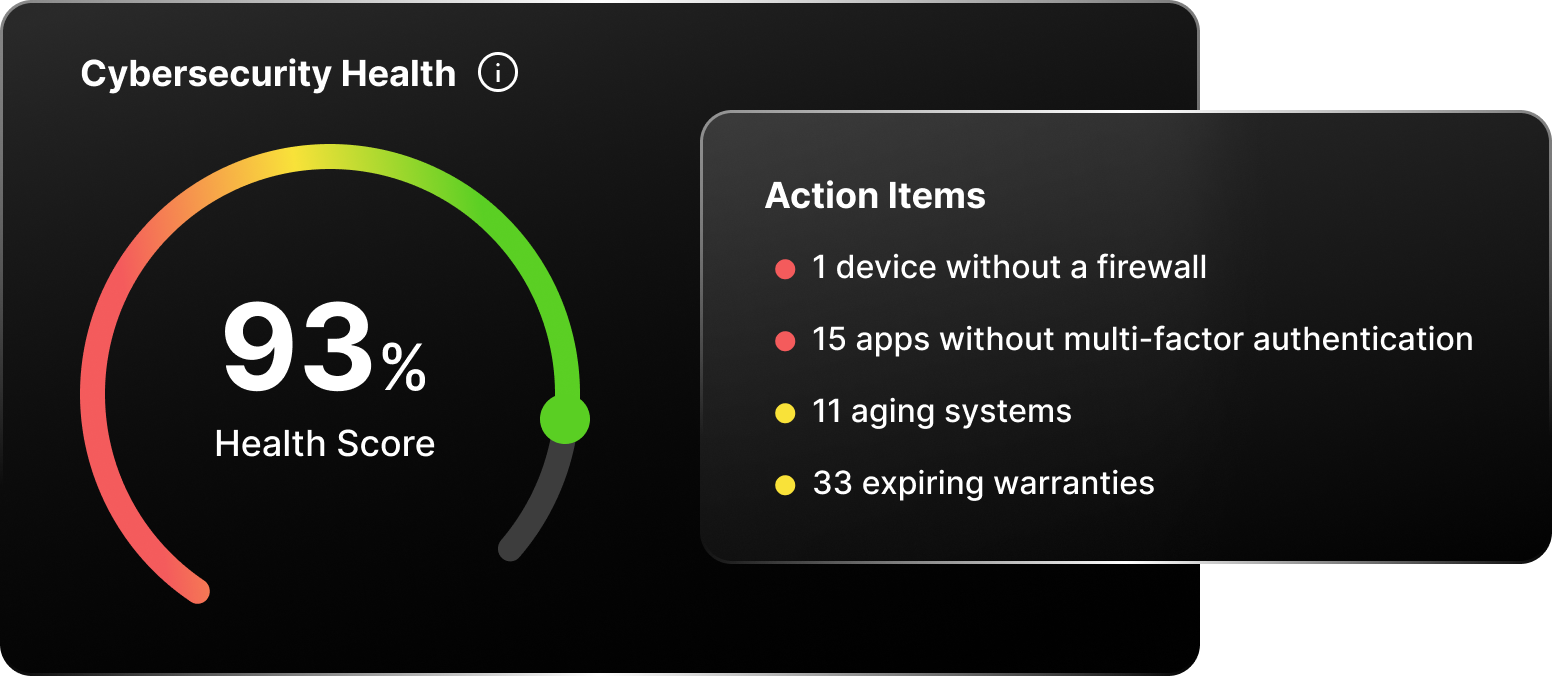
The importance of cybersecurity in modern organizations requires a comprehensive strategy and effective management. BlackPoint promotes a culture of security throughout your organization by developing tailored cybersecurity policies, conducting regular assessments, and providing employee training.

Our cybersecurity team is dedicated to ensuring the security of your IT environment and data. We focus on providing operational security that effectively protects your information and intellectual capital in on-premises and cloud systems.
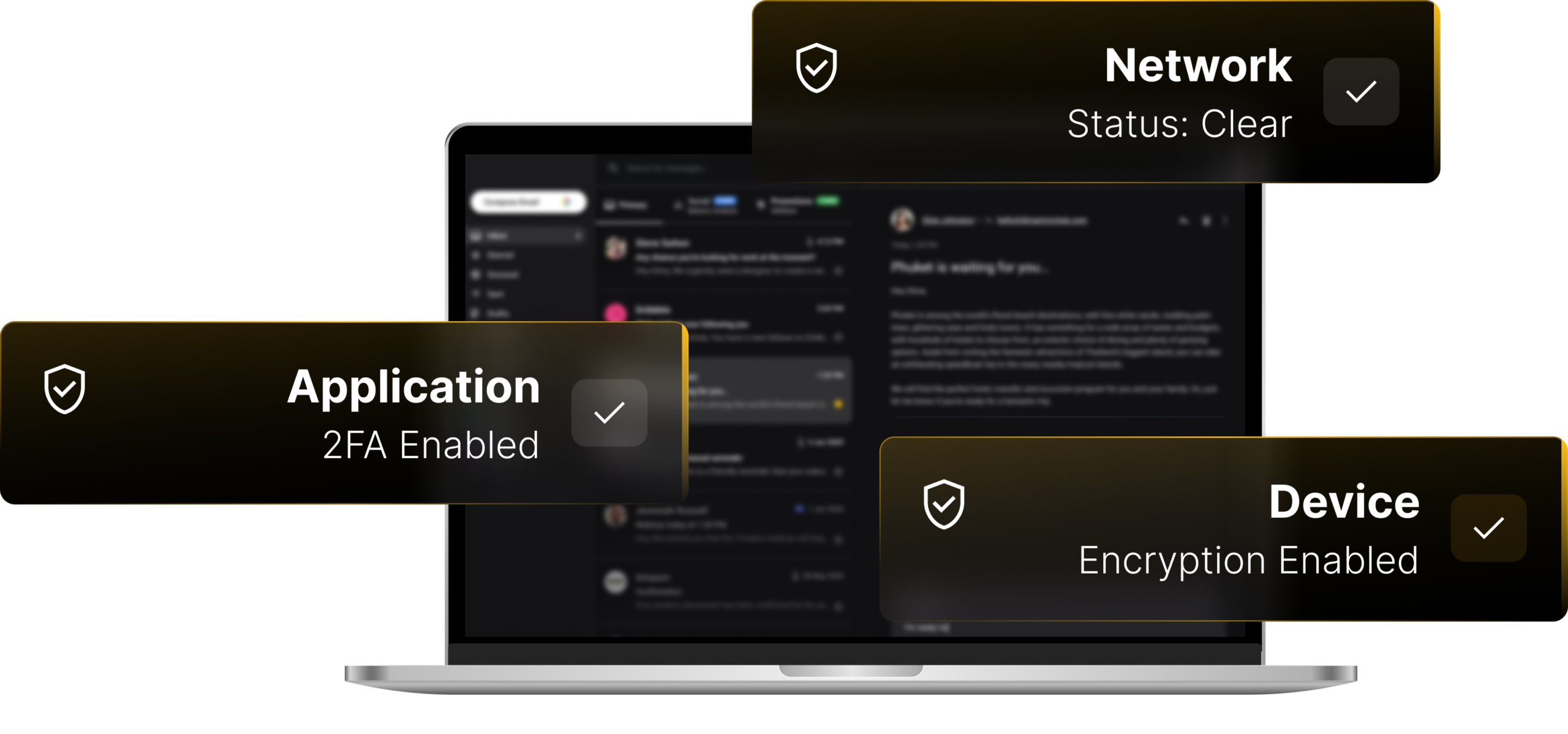
Ransomware attacks and other types of security breaches put your business at risk. Our services focus on preventing security breaches and intrusions to keep your environment safe. BlackPoint’s 24/7 security operations provide the skills necessary to assess, defend, and recover from a security breach.

Advanced security services provide exceptional protection with 24/7 monitoring and response performed with enterprise-grade tools for businesses. In the event of a cybersecurity incident, BlackPoint guarantees that we will get you up and running with absolutely no extra fees or costs.

Cyberattacks are becoming more sophisticated today every day. Threats comes in different forms including malware, phishing, crypto-jacking, SQL injection, and zero-day exploits. Our advanced security services ensure that your endpoints, servers, network, and apps are protected from hackers. If a breach occurs, we guarantee we’ll get your systems up and running without any extra fees or costs.
BlackPoint's next-generation security management service uses advanced threat detection and response technologies to provide your organization with the highest level of protection. Our team will implement and manage these technologies to protect your systems against the latest emerging threats.
Our end-user security training provides education for your employees on security best practices. The training includes customized training modules, assessments, and follow-up coaching, helping your employees stay vigilant against potential threats and promoting a security-focused culture across your organization.
We provide a comprehensive security assessment that looks at your organization's security posture. BlackPoint will identify vulnerabilities and recommend best practices and compliance standards to protect your organization.
BlackPoint's incident remediation and analysis provide support in responding to and remediating security incidents. Our team works quickly to contain and remediate any damage to the IT environment. We perform incident analysis and offer recommendations to improve security and prevent similar incidents in the future.
Ransomware is becoming increasingly dangerous, and attacks now typically include a data exfiltration component. Our security experts help your company avoid ransomware attacks and promptly address the effects to prevent the exfiltration of your data.
Consult with our team of cybersecurity experts for guidance and assistance with all aspects of your organization’s IT security. We can help you design and implement the systems and procedures necessary to protect your environment from increasingly sophisticated and prevalent threat actors.
On detection of an intrusion or malware infection, we isolate the machine from your network and remediate any infections. After isolating machines, we back up your systems and immediately examine how your systems were infected. Finally, after we’ve gathered the necessary details, we send over our analysis and recommendations on how we can prevent them from happening in the future.
Yes. We conduct regular audits and provide you with an in-depth review of your security policies, procedures as well as practices.
We will educate and train your employees on what to watch out for in social engineering attacks and how to protect sensitive data. To test their knowledge, we will execute campaigns to gauge each employee’s interaction with phishing emails.
We will alert you if we detect any information on the dark web and guide you through the steps to secure your sensitive information.
Cybercriminals use malicious software or malware to penetrate systems and access company data. One of the most common ways they spread malware is through deceiving employees to download software. Always be cautious of suspicious emails asking to download new files or follow links to unknown websites.
We offer flexible pricing based on a number of factors such as the size and complexity of your business, number of employees, number of devices, and more. Contact us for a free estimate.